Features include:
- Easy centralized management with federated features
- Cutting edge, crowd-sourced security intelligence
- Threat detection / Alerting / Monitoring
- Full suite of compliance reporting
- Flexible deployment options: cloud, hybrid
- and on-premises
Features of the system
Integrated, Essential Security Controls
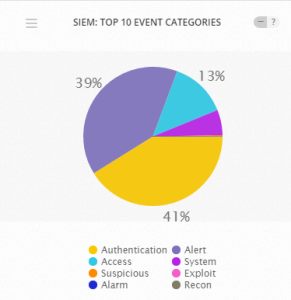
SECURITY INTELLIGENCE/SIEM
- SIEM Event Correlation
- Incident Response
ASSET DISCOVERY
- Active Network Scanning
- Passive Network Scanning
- Asset Inventory
- Host-based Software Inventory
Proactive Network Management
- Log Collection
- Netflow Analysis
- Service Availability Monitoring
THREAT DETECTION
- Network IDS
- Host IDS
- File Integrity Monitoring
VULNERABILITY ASSESSMENT
- Continuous Vulnerability Monitoring
- Authenticated / Unauthenticated Active Scanning