
Introducing Managed Cybersecurity for the digital age.
Done right, by The LCO Group.
Protecting your infrastructure and data has never been more important, or more challenging.
To meet the threats facing our clients in financial services, legal, and other data-heavy industries, The LCO Group re-engineered its security offerings to take advantage of the latest advances and tools available.
We now offer a fully integrated, one-stop offering that addresses key vulnerabilities in modern infrastructures and allow for smaller organizations to not only meet many of the cybersecurity regulations, but have a truly proactive, in-depth tool that will protect your important data ? without breaking the bank to do so.
The heart of this system is threat-based heuristic scanning tool that runs continuously in?real-time on your network and monitors the major threat areas for suspicious behavior. Whether this is from users attempting to login repeatedly from overseas locations, issues affecting the entire network, or anomalous behavior from a single workstation, our ThreatVector system will give us a clear and constant view into the inner workings of?your infrastructure.
Our ThreatVector offering comes in several flavors; the Alarm package offers you basic detection capabilities, the Enhanced offers more advanced detection capabilities, and the Pro system includes remediation.
Features include:
- Easy centralized management with federated features
- Cutting edge, crowd-sourced security intelligence
- Threat detection / Alerting / Monitoring
- Full suite of compliance reporting
- Flexible deployment options: cloud, hybrid
- and on-premises
Features of the system
Integrated, Essential Security Controls
SECURITY INTELLIGENCE/SIEM
- SIEM Event Correlation
- Incident Response
ASSET DISCOVERY
- Active Network Scanning
- Passive Network Scanning
- Asset Inventory
- Host-based Software Inventory
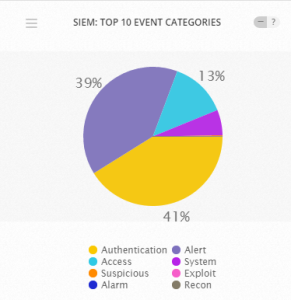
Proactive Network Management
- Log Collection
- Netflow Analysis
- Service Availability Monitoring
THREAT DETECTION
- Network IDS
- Host IDS
- File Integrity Monitoring
VULNERABILITY ASSESSMENT
- Continuous Vulnerability Monitoring
- Authenticated / Unauthenticated Active Scanning

